
This year, the Austrian RISC-V community launched a collaborative initiative aimed at increasing the visibility and impact of the RISC-V ecosystem. The RISC-V meetup, chaired by Daniel Müller-Gritschneder (TU Wien) and Willibald Krenn (Silicon Austria Labs) has gained strong backing from industry leaders such as NXP Semiconductors and Infineon. Their shared goal: to create a strong platform for exchanging knowledge and fostering deep technical dialogue across academia and industry.
 At the second Austrian RISC-V Meetup at Silicon Austria Labs (SAL), Marcel Medwed from NXP in Austria presented the latest developments in microcontroller (MCU) security. His talk focused on how RISC-V instruction set extensions are shaping the future of both physical and logical protection for embedded systems. These efforts are part of the ISOLDE project under the Chips Joint Undertaking, which aims to expand and industrialize the European RISC-V ecosystem.
At the second Austrian RISC-V Meetup at Silicon Austria Labs (SAL), Marcel Medwed from NXP in Austria presented the latest developments in microcontroller (MCU) security. His talk focused on how RISC-V instruction set extensions are shaping the future of both physical and logical protection for embedded systems. These efforts are part of the ISOLDE project under the Chips Joint Undertaking, which aims to expand and industrialize the European RISC-V ecosystem.
The goal? To compete with proprietary alternatives by delivering high-performance, secure processing platforms tailored for automotive, smart cities, mobility, and logistics.
Embedded systems face a range of attacks, from clock and power glitches that can cause timing violations, to memory vulnerabilities like buffer overflows. These attacks can lead to skipped instructions, faulty data, privilege escalation, and even arbitrary code execution.


The challenge lies in designing security mechanisms that are both robust and efficient, minimizing impact on code size and hardware footprint.
To address these threats, the ISOLDE project has developed a comprehensive suite of RISC-V extensions and custom security mechanisms:
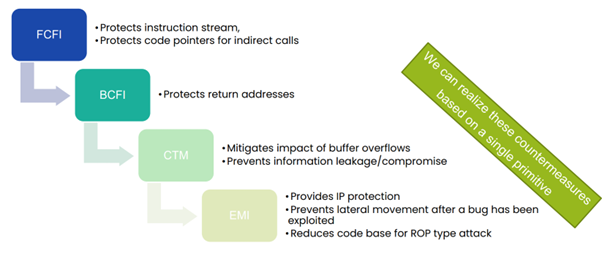
Security for embedded systems must be both effective and lightweight, ensuring robust protection without unnecessarily increasing code size. By leveraging RISC-V instruction set extensions and custom mechanisms, developers can implement targeted and efficient security features. Within the ISOLDE project, a comprehensive "cocktail" of countermeasures has been developed to address both fault-based and software-based attacks, providing a holistic approach to embedded system security.